Beyond Bitcoin: An In-Depth Look At Blockchain Consensus Mechanisms
March 4, 2025
Introduction
Digital monetary transactions have been completely transformed by the advent of blockchain technology, which makes it possible and even easy for decentralized, safe, and transparent transactions to take place across the entire network without needing middlemen. Every blockchain instance requires a consensus mechanism at its core to ensure that users of the network achieve agreement on the legitimacy of all actions and record transactions in an accurate and incorruptible way.
By eliminating central authority control, distributed ledger technology increases effectiveness, security, and trust across blockchain networks. Adopting the consensus mechanism method not only protects the integrity of the whole network but also prevents harmful behaviours such as fraudulent spending, data tampering, and unlawful information modifications.
There are several consensus models, each meant to deal with specific requirements and limitations across various blockchain situations. From the resource-efficient Proof of Stake (PoS) to the energy-intensive Proof of Work (PoW), along with recently developed alternatives such as the Delegated Proof of Stake (DPoS) and the Practical Byzantine Fault Tolerance (PBFT), all consensus models form the basis for safe and trustworthy blockchain operations.
This blog will examine how different models operate, their advantages and disadvantages, and how they impact blockchain technology’s scalability, security, and efficiency. The content that follows will aid you in understanding the crucial role consensus mechanisms play in forming decentralized ecosystems, regardless of whether you’re a blockchain developer, company executive, or industry expert wishing to integrate blockchain solutions.
Explaining Blockchain Consensus Mechanisms
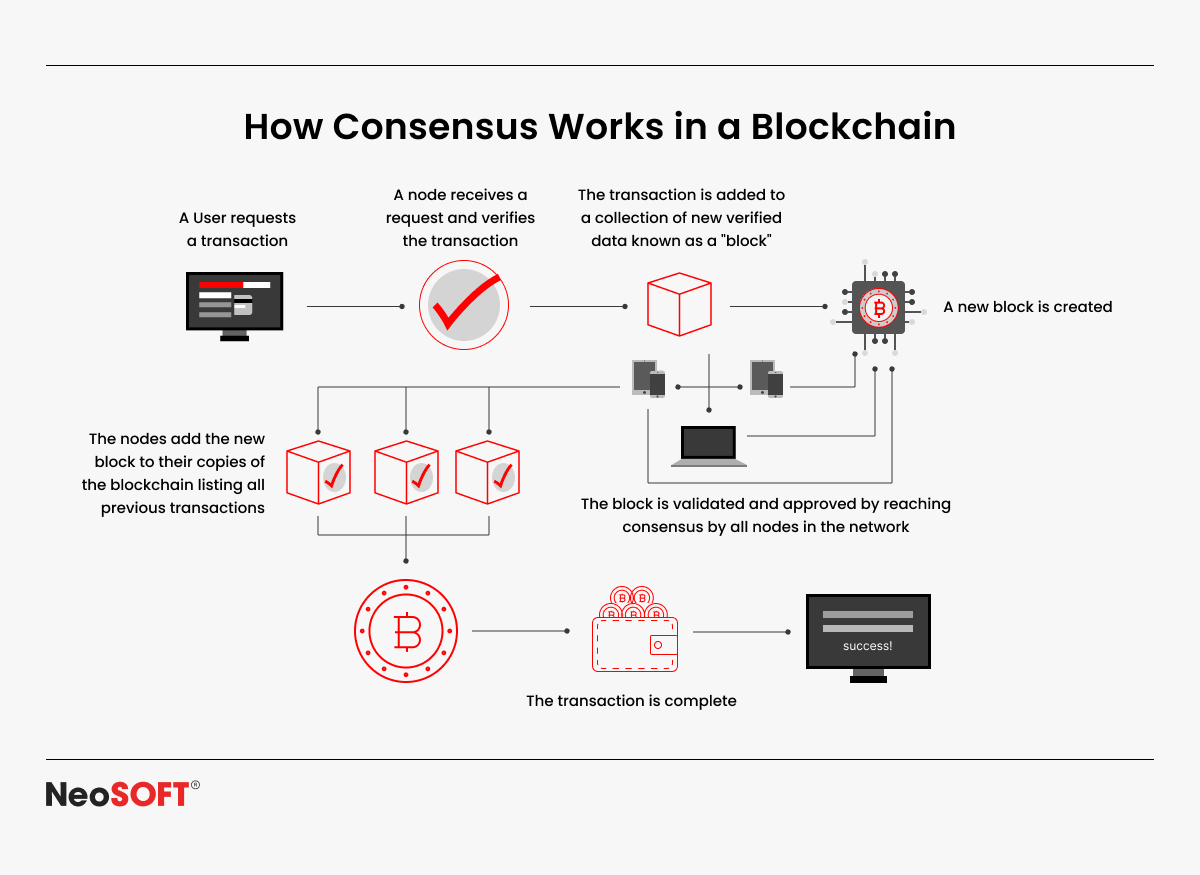
The basic procedure by which participants in blockchain systems agree on the validity and sequence of transactions is known as a consensus mechanism. A blockchain consensus mechanism considerably ensures that all distributed nodes keep a synchronized, impenetrable ledger to validate transactions, in contrast to conventional databases or financial systems that depend on a central authority for validation. By getting rid of single points of failure, this decentralized strategy lowers the possibility of fraud and increases network resilience.
For a blockchain to remain functional and intact, consensus mechanisms are essential. By making sure that every node adheres to the same guidelines for authenticating transactions and creating new blocks, these cryptographic techniques can protect against irregularities and unwanted changes. Blockchain networks can be susceptible to double-spending, security lapses, or inefficiencies that jeopardize their dependability in the absence of a strong consensus model.
In blockchains, consensus mechanisms ensure that all the nodes maintain an impartial and immutable record rather than depending on a single authority to handle validation. The ability of this consensus protocol to facilitate smooth communication between network participants makes it essential to the operation of blockchain networks. The core tenets of blockchain – security, decentralization, and zero-trust cooperation – are maintained by consensus mechanisms, which orchestrate these interactions between network participants.
Effective consensus procedures are necessary for both private and public blockchains. They keep public networks accessible and transparent while preventing bad actors from altering the ledger. They provide decentralized validation and assist enterprises in enforcing stringent security requirements in private or permissioned blockchains. The consensus layer that a blockchain uses determines how effective it is since several existing consensus mechanisms weigh trade-offs amongst security, speed, scalability, and energy efficiency.
Key Characteristics of Consensus Algorithms
Decentralized networks utilize blockchain consensus models since they share some essential characteristics, which are as follows:
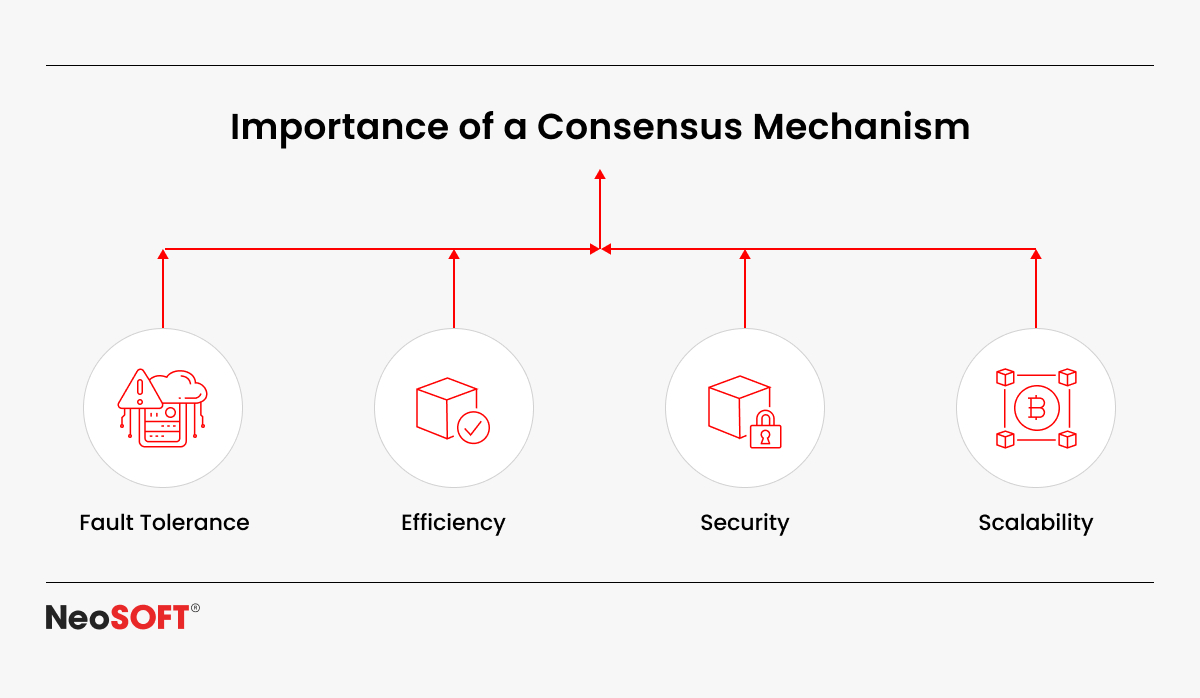
- Fault Tolerance: A good consensus model is made to function well even in the unlikely circumstance that some participants appear unreliable or behave poorly. Ensuring consistency in hostile instances necessitates this resilience.
- Efficiency: The process to achieve consensus requires an effective use of the time and resources available. Multiple methods, like PoW and PoS, prioritize efficiency significantly while often balancing speed and security.
- Security: Consensus algorithms must protect the network from hazards such as Sybil attacks, in which a hacker establishes several false identities to gain control of the system. Efficient systems have been established to reduce such risks.
- Scalability: Consensus mechanisms require flexibility as blockchain networks expand in order to deal with higher quantities of transactions while retaining security and performance.
As the cornerstone of blockchain technology, these different consensus algorithms assure the reliability, security, and legitimacy of decentralized networks.
Even though they satisfy the specific needs of different blockchain applications, such as supply chain management, smart contracts, and digital currency management, plenty of the models that we will be talking about below have pros and cons.
Types Of Consensus Mechanisms
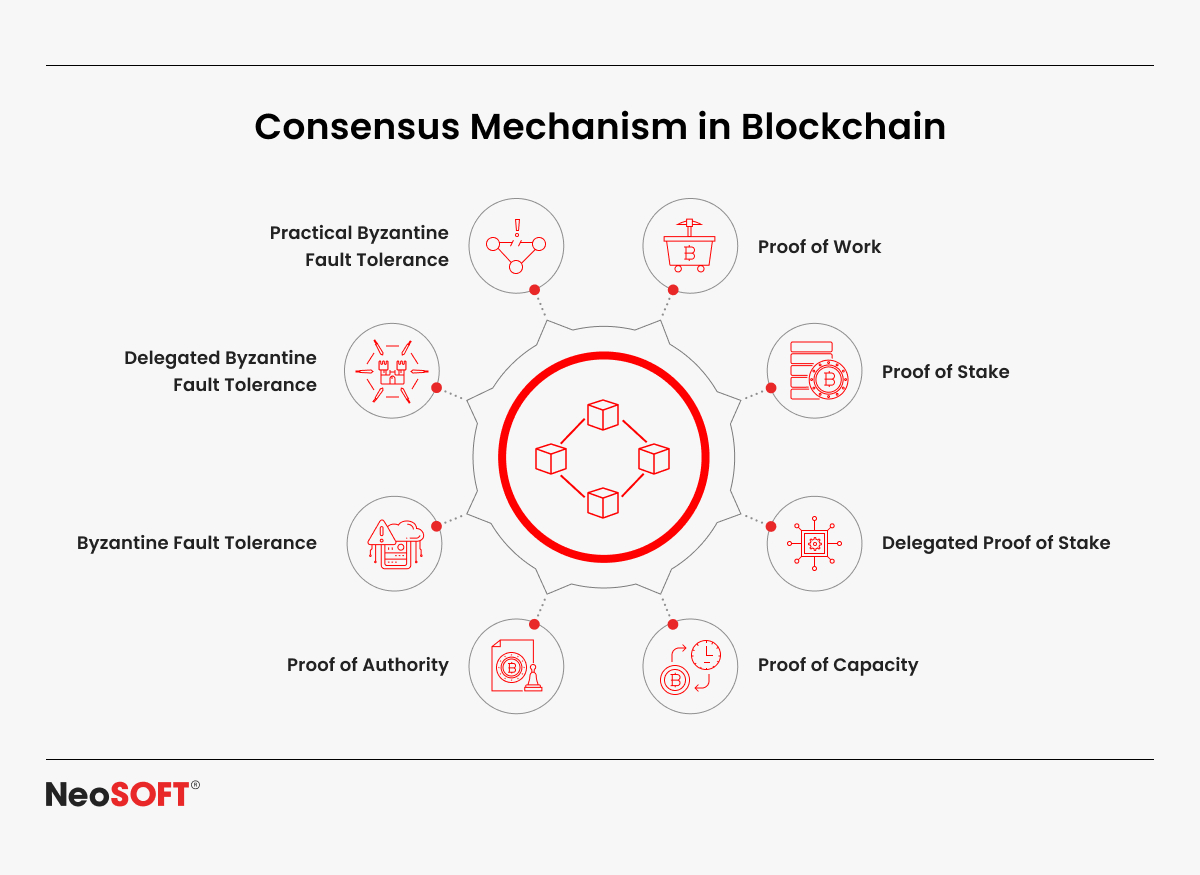
Proof of Work (PoW)
PoW is one of the most popular consensus mechanisms, where miners are required to solve difficult puzzles to add blocks by certifying transactions to receive block rewards. It ensures higher security and decentralization but faces challenges when it comes to significant computational power consumption. The system dynamically keeps altering the puzzles for stable block generation. Bitcoin, the first cryptocurrency, uses PoW to maintain a secure and immutable ledger.
Proof of Stake (PoS)
PoS is a consensus mechanism that uses staking in lieu of energy-intensive mining, where validators lock up cryptocurrency to authenticate and verify transactions and add blocks. It requires less energy than PoW because selection is dependent on stake size and duration. PoS thus promises benefits like lower hardware requirements and decentralization but faces risks such as centralization by large stakeholders and high staking thresholds along with security concerns like long-range attacks. It is a scalable and sustainable substitute that is gaining widespread acquisition.
Delegated Proof of Stake (DPoS)
Token owners select a limited number of validators who govern the blockchain by accepting transactions and adding new blocks through the DPoS process. DPoS is known to enhance speed, scalability, and efficiency, but it risks centralization as power gets concentrated among a few validators. In order to push for fairness, validators rotate, and voting power is proportionate to token holdings. EOS is a great example, utilizing DPoS for high transaction throughput and scalable decentralized applications, which makes it ideal for networks prioritizing performance over decentralization.
Proof of Authority (PoA)
A validator-based consensus mechanism, PoA, was developed for private blockchains and depends on reliable validators chosen for their reputation and verification rather than their ownership or processing power. Since it ensures a more reliable and effective new block creation, PoA is suited for high-throughput enterprise applications that demand validator accountability. For example, PoA is incorporated into VeChain for quick and safe supply chain management and transaction fee processing. However, its drawbacks include centralization resulting from a restricted amount of validators and lower transparency in comparison with public blockchains.
Proof of Capacity (PoC)
Proof of Capacity is a consensus process that uses data storage rather than computational capacity to validate transactions and build new blocks. Miners prepare cryptographic data (plots) and keep it on their hard drives. When a new block is required, the stored data is analyzed to decide the winner. When opposed to PoW, PoC is much more energy efficient and doesn’t need sophisticated mining hardware. However, it requires a lot of storage space and is vulnerable to pre-mining assaults. Blockchains such as Burstcoin (BURST) use PoC for sustainable and decentralized mining.
Byzantine Fault Tolerance (BFT)
It is a property of distributed ledgers that are able to function correctly even if some nodes act fraudulently or fail unpredictably. The problem associated with it is that the independent players must reach a consensus despite flawed or dishonest actors. In distributed databases like blockchain, BFT is essential, where consensus must be upheld under hostile circumstances.
Practical Byzantine Fault Tolerance (PBFT)
It is a type of BFT consensus approach that has been improved for permissioned networks, in which some honest nodes are relatively known and trusted. It requires 3f+1 nodes to tolerate faulty or malicious nodes and to adopt a leader-replica paradigm to reach consensus throughout a three-phase procedure (Pre-prepare, Prepare, and Commit). Whilst PBFT can have scalability issues in big networks, its low latency and high security make it an ideal choice for enterprise blockchain solutions like Hyperledger Fabric.
Delegated Byzantine Fault Tolerance (DBFT)
Evolved from PBFT, this consensus mechanism is designed for public blockchain networks like NEO. In order to obtain a consensus on their behalf, token holders must choose validators under the new delegated voting method. Compared to PoW, this model reduces computing power and overhead while preserving fault tolerance and improving scalability and efficiency of blockchain nodes. However, network security is dependent on the honesty of elected delegates due to the potential of validator collusion introduced by DBFT.
Comparison overview of the blockchain consensus mechanisms
Consensus processes are essential to blockchain networks’ efficiency, decentralization, and security. But since every model has trade-offs, it’s important to assess them according to criteria like governance, scalability, and energy consumption.
Although Proof of Work (PoW), which was utilized in early Ethereum and Bitcoin, provided great security, it was sluggish and energy-intensive. Additionally, mining pools can reduce decentralization by centralizing control. Proof of Stake (PoS), which transfers the validation process over to token holders in order to solve these problems, increases efficiency but runs the danger of causing wealth concentration, in which larger stakeholders have greater sway.
By letting token owners choose a select few delegates to validate blocks and transactions, Delegated Proof of Stake (DPoS) improves Proof of Stake. This makes things faster and more scalable, but it also consolidates power in a small number of hands, which could compromise decentralization. For efficiency and governance, networks like Tron and EOS use DPoS.
Byzantine Fault Tolerance (BFT) methods adopt a different strategy, depending on structured communication instead of financial rewards. They are quite effective; however, they have scalability issues. Through a leader-driven procedure, Practical BFT (PBFT) improves this, which makes it perfect for private blockchains such as Hyperledger Fabric. NEO uses Delegated BFT (DBFT), which combines fault tolerance and delegation to further increase efficiency.
Alternative validation techniques are the main focus of emerging consensus models. Token destruction is a requirement for Proof of Burn (PoB), whereas data storage space is used in place of processing power for Proof of Space (PoSpace) and Proof of Capacity (PoC). Proof of Authority (PoA) is appropriate for private blockchains since it depends on reliable validators. Other techniques, such as Proof of History (PoH) and Proof of Elapsed Time (PoET), optimize transaction security and speed.
Each consensus algorithm has its own advantages and disadvantages, making them appropriate for certain scenarios:
- PoW works well for energy-intensive but highly secure networks like Bitcoin.
- PoS is more efficient and environmentally friendly but introduces the risk of wealth centralization.
- DPoS increases scalability but sacrifices decentralization.
- BFT and PBFT are well-suited for permissioned blockchains with high-security needs.
- DBFT optimizes efficiency and security for enterprise applications but relies on a limited number of delegates.
Some place a higher priority on decentralization, while others concentrate their computational resources on energy efficiency or scalability. Whether security, speed of transactions, or a hybrid method are the top priorities will determine which consensus algorithm is the best option for a blockchain. Future blockchain innovation will continue to be shaped by innovative, hybrid, and other consensus algorithms as the technology develops further.
Conclusion
The decision on which blockchain consensus algorithms to use is influenced by a number of factors, including the specific application in question, the network’s size, security, scalability, affordability, and compliance issues. Current consensus processes, each with their own pros and weaknesses, serve as the foundation for secure, decentralized networks.
PoW ensures robust security at the cost of energy consumption, whereas PoS and its variations boost scalability and efficiency. BFT-based solutions are perfect for business and permissioned networks because they offer strong fault tolerance. Network structure, scalability, storage capacity, transaction speed, and security requirements all play a role in choosing the best consensus model.
Next-generation hybrid consensus mechanisms are being developed as blockchain technology progresses further in order to increase security, streamline operations, process transactions, and become energy efficient. For developers and companies looking to use blockchain for a variety of applications, keeping up with these developments is essential.
Blockchain is rapidly changing many industries, and thus, developers, companies, and enthusiasts must explore its potential. Selecting the best blockchain solution, promoting innovation, and influencing the decentralized environment all benefit from a thorough understanding of the various consensus methods.
To learn more about how our skilled teams of developers can support you in creating scalable and secure decentralized blockchain applications, contact info@neosofttech.com for state-of-the-art blockchain solutions customized to your requirements.
Recommended