Secure, Simplify, Succeed: Proven Strategies for Effective Endpoint Management
December 26, 2024
Introduction
In today’s dynamic IT environment, endpoint management has become an essential part of effective infrastructure and cybersecurity. The proliferation of electronic devices, from laptops and smartphones to IoT devices, has made it more difficult for businesses to manage and safeguard that environment.
The task is much more difficult now that employees can access vital company information from a variety of devices and locations, owing to the growing popularity of hybrid and remote work. In addition to complicating network access management, endpoint mobility and diversity offer up additional avenues for security threats.
In order to give IT organizations useful insights to improve security, streamline operations, and maintain compliance in this rapidly changing digital age, this blog will examine realistic endpoint management techniques and best practices. It is intended for system administrators, IT leaders, and other tech workers looking for practical ways to simplify their endpoint management system administration.
The Value of Efficient Endpoint Management
Defining Endpoint Management
The administration, security, configuration, and monitoring of any endpoint device on a company’s network are all part of endpoint management. Any devices that are linked to the network, including desktops, tablets, smartphones, laptops, Iot devices, and more, can be considered an endpoint. The objective is to maintain these devices’ functionality, security, and adherence to all company guidelines.
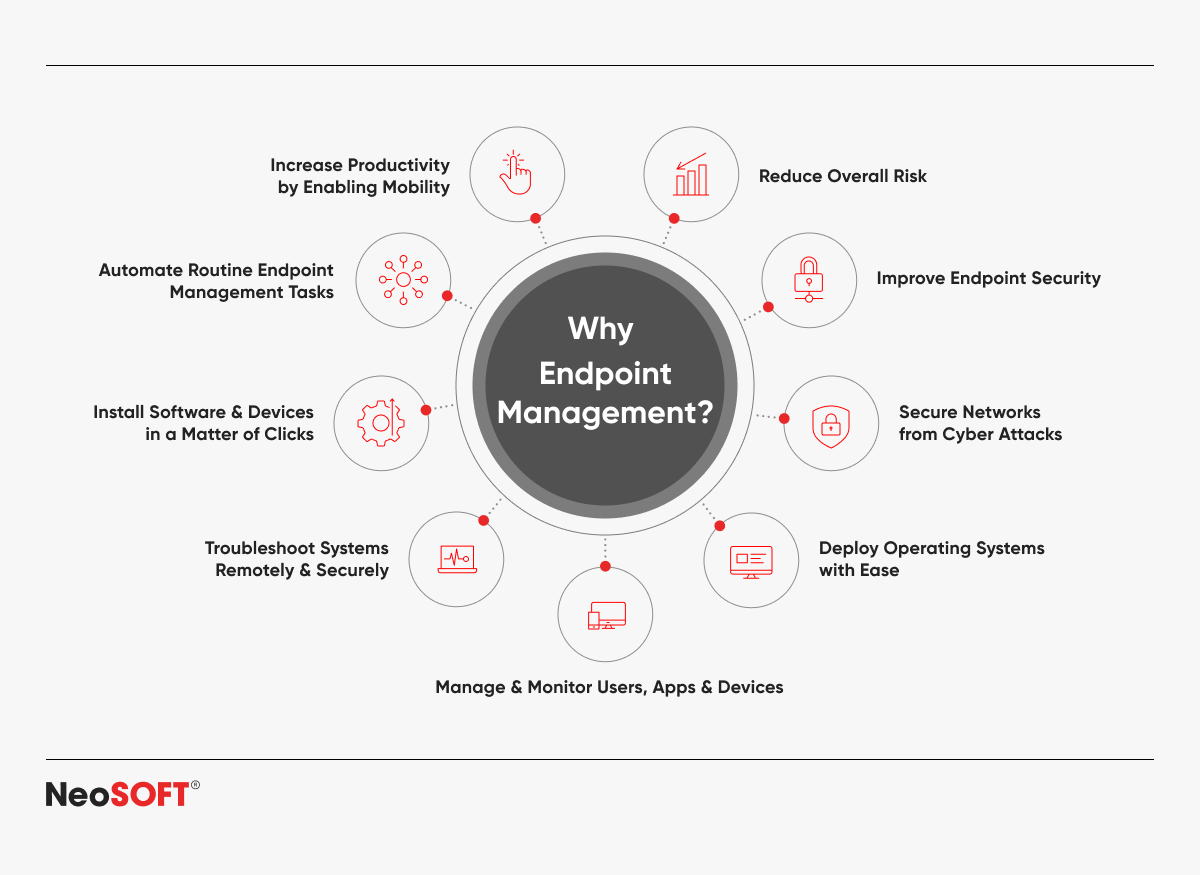
Why is Endpoint Management Crucial?
Keeping Company Information Safe and Reducing Security Vulnerabilities: Endpoint management is crucial in protecting sensitive company information from advanced threats. Organizations can reduce vulnerabilities and minimize cyber attack risks by deploying strong security measures such as endpoint encryption, secure multiple-factor authentication (MFA), and timely patch updates.
Ensuring Compliance with Regulatory Standards: Privacy and data security in many firms are governed by stringent legislation such as GDPR, HIPAA, and ISO principles. By ensuring that authorized users and all linked devices follow these guidelines, proper endpoint management lowers the possibility of fines for non-compliance or harm to one’s reputation.
Improving User Experience and Employee Productivity: Endpoints that are properly maintained see fewer interruptions from malware, obsolete software, and incorrect setups. Proactive monitoring and troubleshooting improves the user experience by preventing unnecessary downtime so that employees can concentrate on their work.
Endpoint management software is thus not merely a technical requirement; it is also a strategic facilitator of operational effectiveness, security, and business continuity.
Key Challenges to Effective Endpoint Management
The complexity of endpoint management has increased dramatically as businesses adopt flexible work arrangements and digital transformation. The following are the main obstacles that IT teams encounter when handling endpoints:
Managing an Increasingly Diverse Endpoint Array
A growing variety of devices are used in the modern office, ranging from conventional desktops and laptops to mobile phones, IoT devices, as well as virtual endpoints. It can be challenging to keep setup, updates, and security rules uniform across all device types because each has unique requirements.
Managing Security Risks in Hybrid and Remote Work Settings
The area of attack for cyber risks has increased as a result of employees accessing corporate data and company resources from different locations, frequently on unprotected or personal devices. While making sure sensitive data is protected, IT staff must deal with problems like obsolete software, unprotected networks, and lax access controls.
Maintaining Device Performance, User Convenience, and Security
User productivity can occasionally be hampered by strict security measures, which can cause irritation and possibly compromise security via workarounds. For endpoint management methods, striking the correct balance between strong security and a smooth user experience is a constant challenge.
Addressing these difficulties necessitates a deliberate, dynamic strategy for an endpoint management solution that takes into account both technical and human concerns, ensuring operational efficiency while maintaining security.
Best Practices for Successful Endpoint Management
Organizations must combine strategic planning, strong tools, and user-focused activities to manage and protect endpoint devices. Given below are some top techniques for optimizing endpoint management:
Create a Thorough Endpoint Management Plan
The cornerstone of efficient endpoint management is a thorough plan. To guarantee consistency among devices, and enforce security policies, organizations should establish explicit policies that control endpoint usage, safety, and maintenance. In order to assist businesses maintain operational efficiency whilst abiding by industry standards, these policies must be in line with organizational goals and compliance needs.
Invest in Tools for Centralized Endpoint Management
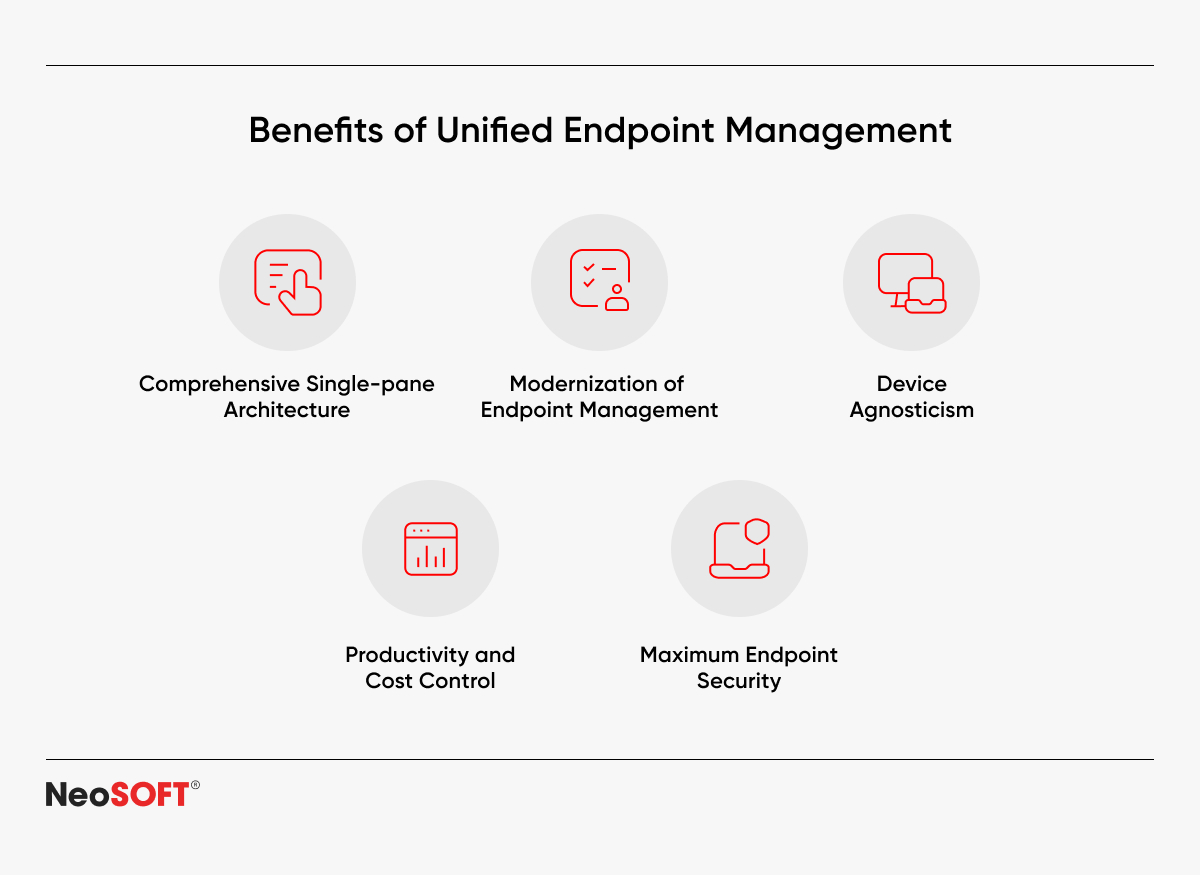
IT professionals can manage a variety of devices from a single interface with centralized tools like Unified Endpoint Management (UEM) platforms. These solutions promote automated updates, enable remote access and real-time monitoring, and expedite troubleshooting procedures. Organizations may improve overall device performance, limit downtime, and eliminate human labor by integrating endpoint management software.
Give Priority to Endpoint Security
An essential part of any management plan is endpoint security. Endpoint encryption and multi-factor authentication (MFA) should be used to shield private and sensitive information from unwanted access. Routine software and operating system upgrades are crucial for fixing vulnerabilities, even though Endpoint Detection and Response (EDR) programs can proactively identify, assess, and mitigate potential security threats.
Facilitate Automation for Increased Productivity
The key to keeping an endpoint ecosystem under control is automation. By implementing software updates and patch management automation, enterprises can guarantee that devices remain secure and up to date. Frequent backups, security patches and threat assessments protect data and identify possible problems before they become serious, which improves security significantly.
Provide Training and Support to Users
The effectiveness of endpoint management initiatives depends on user support and awareness. Endpoint security recommended practices, like identifying phishing attempts, avoiding dangerous activities, and setting strong passwords, should be taught to staff members. Additionally, to minimize disruptions and promote a pleasant user experience, a devoted support system needs to be in place that quickly addresses endpoint concerns.
By putting these best practices into reality, businesses can build an endpoint environment that is safe, effective, and encourages productivity while safeguarding important data and adhering to industry standards.
Strategies for Proactive Threat Mitigation
Proactively addressing endpoint security is key. Companies must foresee and prevent threats before they have an opportunity to cause harm rather than merely reacting to them. A few ways to do this are:
Real-time Detection of Threats
Real-time risk monitoring is made possible by integrating endpoint management systems with sophisticated threat detection tools. Organizations can swiftly address concerns before they become serious breaches by establishing warnings for questionable activity.
Artificial Intelligence and Machine Learning
Machine learning and artificial intelligence are both powerful tools that can be utilized to identify security risks and unusual activity accurately. Large volumes of data are analyzed by these technologies in order to identify irregularities, forecast dangers, and automate responses, enabling quicker and more efficient threat mitigation.
Zero Trust Architecture
One important tactic for restricting access to only authenticated individuals and devices is to put Zero Trust principles into practice. Zero Trust greatly reduces the attack surface and improves security across endpoints by making no one, inside or outside of the network, trusted by default.
Network Segmentation
In order to restrict the lateral movement of threats, network segmentation entails splitting the network into discrete areas. Segmentation can contain an attack in the event of a breach, limiting any harm and stopping it from propagating throughout the network.
Advanced Monitoring
Early detection of vulnerabilities and questionable activity is facilitated by powerful analytics and ongoing endpoint monitoring. Organizations can use these technologies to identify departures from typical behavior and fix security flaws before attackers take advantage of them.
A more robust defense against new attacks is ensured and an organization’s endpoint security is strengthened when threats are proactively mitigated using these techniques.
Top Endpoint Management Software Solutions
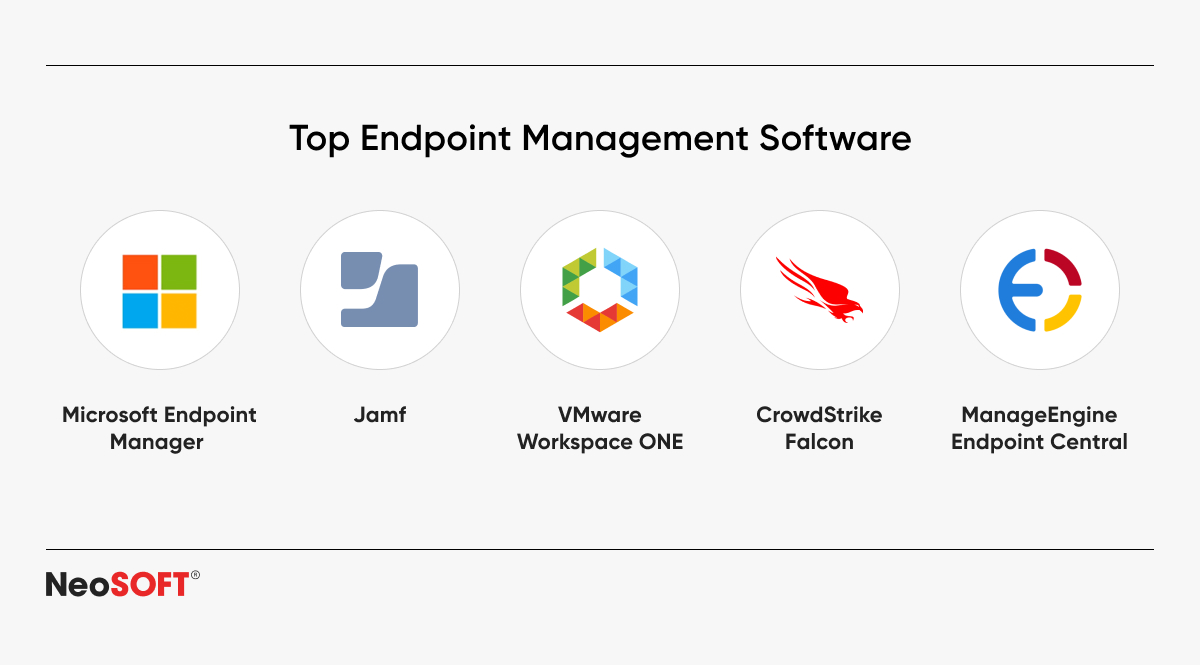
Selecting the appropriate endpoint management software is an important step in securing and optimizing your IT environment. The best solution is determined by the size of your firm, its specialized needs, and budget. Here are some recommended tools:
- Microsoft Endpoint Manager – It provides easy connection with Windows and Microsoft 365, which renders it perfect for enterprises that already use both platforms.
- Jamf – Tailored for enterprises that use Apple devices, this solution offers superior administration and protection for macOS and iOS.
- VMware Workspace ONE – A powerful UEM solution that supports several platforms and is appropriate for a wide range of IT environments.
- CrowdStrike Falcon – Offering sophisticated threat identification and response capabilities, this product is centered on endpoint security.
- ManageEngine Endpoint Central – Combines simplicity of use with a variety of functions, such as patch management and deployment of software.
The correct endpoint management software is critical for improving security, increasing efficiency, and ensuring compliance. To reinforce your endpoint management strategy, consider the options above and select a solution that corresponds with the goals of your business.
Metrics for Continuous Endpoint Management Success
Effective endpoint management necessitates not just the execution of best practices, but also a reliable system for monitoring progress. Establishing set Key Performance Indicators (KPIs) enables firms to assess the efficiency of their endpoint management policies and pinpoint areas for improvement.
The frequency and effectiveness of software upgrades and patch deployments to protect devices, the average time it takes to resolve endpoint-related issues, and the rate of adherence to endpoint security policies are a few crucial KPIs. Additionally, indicators like device uptime, user happiness, and the number of security events found and fixed offer important information about how well endpoint management programs are doing overall.
Keeping up with the constantly changing IT ecosystem requires constant strategy monitoring and upgrading. Emerging cyber threats and the introduction of new devices and technologies are two examples of new issues that force enterprises to review their endpoint management procedures periodically.
Through performance data analysis and user and IT team feedback, organizations can make well-informed adjustments to improve user experience, streamline processes, and strengthen security. Long-term effectiveness, adaptability, and alignment with corporate objectives are guaranteed by measuring achievement and making a commitment to continual development.
Conclusion
Effective endpoint management is crucial for maintaining security, streamlining operations, and satisfying regulatory requirements in the ever changing digital landscape of today. Strong endpoint management methods are more important than ever as businesses adopt hybrid and remote work environments and depend more and more on a large variety of devices.
Now is the perfect moment to improve your endpoint management procedures. Begin by assessing your present procedures, spotting any gaps, and putting plans in place to close them. Our team is here to assist people who are looking for professional advice.
At NeoSOFT, we provide complete endpoint management solutions that are tailored to the requirements of your company. Partner with us to benefit from our smooth management tool implementation, continuous maintenance and monitoring assistance, and professional advising to create strong strategies. Reach out to us today at info@neosofttech.com to find out how we can help you succeed!
Recommended